By Carl Maverick Pascual (Threats Analyst) Cybercriminals continue to use cryptocurrency-mining malware to abuse computing resources for profit. As early as 2017, we have also observed how they have applied fileless techniques to make detection and monitoring more difficult. On August 2, we observed a fileless cryptocurrency-mining malware, dubbed GhostMiner, that weaponizes Windows management instrumentation… Continue reading Fileless Cryptocurrency-Miner GhostMiner Weaponizes WMI Objects, Kills Other Cryptocurrency-Mining Payloads
Month: September 2019
There She Breaches! Watch Out For Your Identity Data!
Data breaches keep on coming. Here’s what you can do to stay ahead of the hackers Money makes the world go around. It’s the glue that holds our society together and the engine that drives our economy. But it’s also coveted by a growing global population of highly resourceful and determined cyber-criminals. They’re out to… Continue reading There She Breaches! Watch Out For Your Identity Data!
Magecart Skimming Attack Targets Mobile Users of Hotel Chain Booking Websites
We discovered a series of incidents where the credit card skimming attack Magecart was used to hit the booking websites of chain-brand hotels — the second time we’ve seen a Magecart threat actor directly hit ecommerce service providers instead of going for individual stores or third-party supply chains. Back in May, we discovered a new… Continue reading Magecart Skimming Attack Targets Mobile Users of Hotel Chain Booking Websites
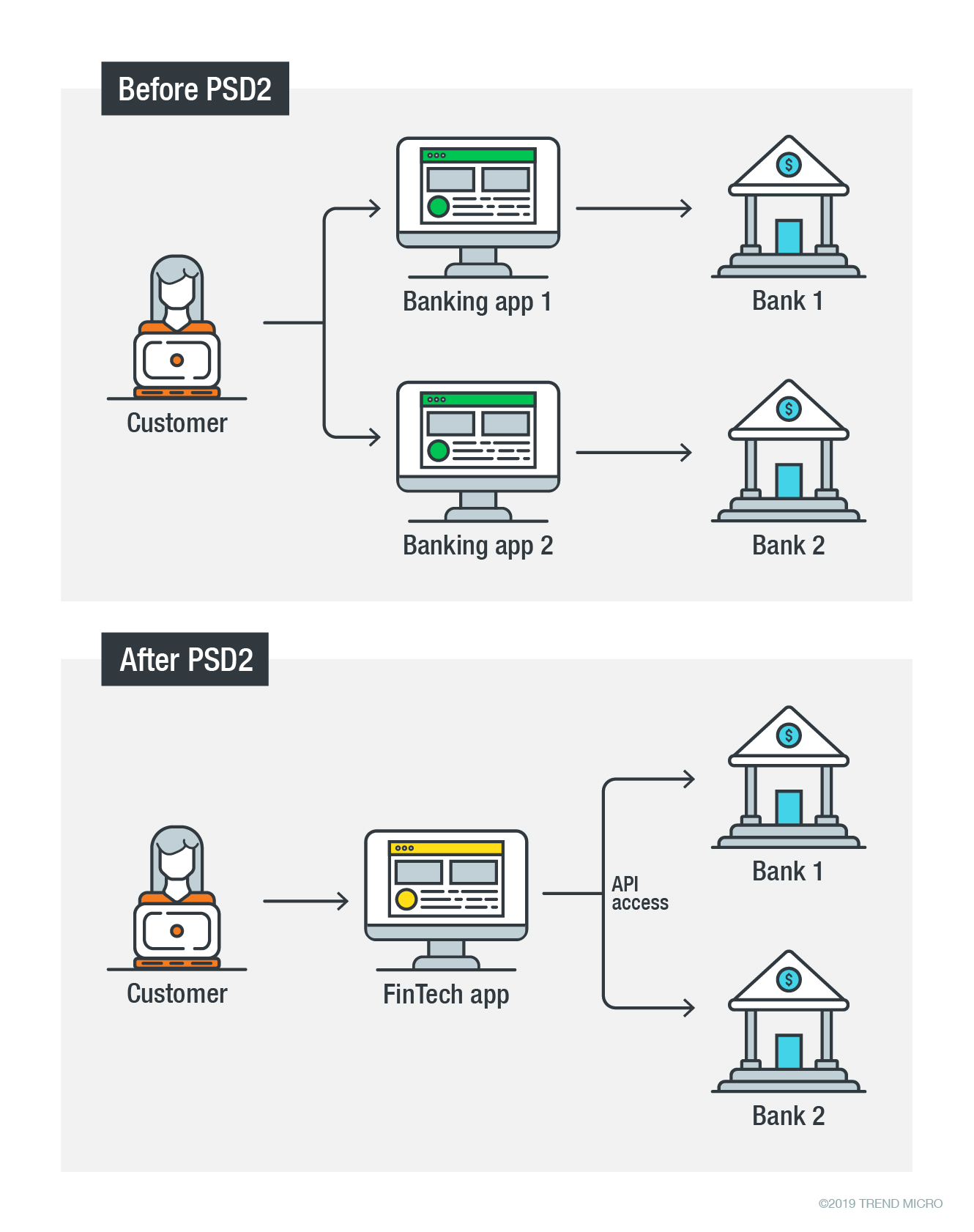
When PSD2 Opens More Doors: The Risks of Open Banking
By Feike Hacquebord, Robert McArdle, Fernando Mercês, and David Sancho As more industries adapt to cater to the increasingly mobile market, the financial industry is the latest to experience a shake-up. The Revised Payment Service Directive (PSD2) – also known as Open Banking – is a new set of rules for the European Union (EU)… Continue reading When PSD2 Opens More Doors: The Risks of Open Banking
Skidmap Linux Malware Uses Rootkit Capabilities to Hide Cryptocurrency-Mining Payload
By Augusto Remillano II and Jakub Urbanec (Threat Analysts) Cryptocurrency-mining malware is still a prevalent threat, as illustrated by our detections of this threat in the first half of 2019. Cybercriminals, too, increasingly explored new platforms and ways to further cash in on their malware — from mobile devices and Unix and Unix-like systems to… Continue reading Skidmap Linux Malware Uses Rootkit Capabilities to Hide Cryptocurrency-Mining Payload
This Week in Security News: IoT Devices Are a Target in Cybercriminal Underground
Welcome to our weekly roundup, where we share what you need to know about the cybersecurity news and events that happened over the past few days. This week, learn how fileless malware abuses PowerShell. Also, read how Trend Micro researchers are pulling back the curtain on the cybercriminal underground to warn consumers and businesses about… Continue reading This Week in Security News: IoT Devices Are a Target in Cybercriminal Underground
Hacking LED Wristbands: A ‘Lightning’ Recap of RF Security Basics
By Jonathan Andersson and Federico Maggi Early this year, we published a security analysis of industrial radio remote controllers. In that research, we examined different vulnerabilities in the implementation of radio frequency (RF) communication and the possible impact of an attack on these weaknesses. We believe that RF security research is of great importance especially… Continue reading Hacking LED Wristbands: A ‘Lightning’ Recap of RF Security Basics
From BinDiff to Zero-Day: A Proof of Concept Exploiting CVE-2019-1208 in Internet Explorer
By Elliot Cao (Vulnerability Researcher) Last June, I disclosed a use-after-free (UAF) vulnerability in Internet Explorer (IE) to Microsoft. It was rated as critical, designated as CVE-2019-1208, and then addressed in Microsoft’s September Patch Tuesday. I discovered this flaw through BinDiff (a binary code analysis tool) and wrote a proof of concept (PoC) showing how… Continue reading From BinDiff to Zero-Day: A Proof of Concept Exploiting CVE-2019-1208 in Internet Explorer
September Patch Tuesday Bears More Remote Desktop Vulnerability Fixes and Two Zero-Days
Microsoft’s September Patch Tuesday covered 80 CVEs, 17 of which were rated critical, and included patches for Azure DevOps Server, Chakra Scripting engine, and Microsoft SharePoint. Sixty-two were labeled as important and included patches for Microsoft Excel, Microsoft Edge, and Microsoft Exchange. Only one was rated as moderate. Remote desktop vulnerabilities Continuing the trend from… Continue reading September Patch Tuesday Bears More Remote Desktop Vulnerability Fixes and Two Zero-Days
Are IoT Threats Discussed In The Cybercriminal Underground?
With IoT devices expected to reach tens of billions in the next few years, is it any wonder that cybercriminals are looking for ways to take advantage of this massive attack surface to generate illicit money? A number of Trend Micro researchers from around the globe decided to look into this and launched a research… Continue reading Are IoT Threats Discussed In The Cybercriminal Underground?