by Cedric Pernet, Vladimir Kropotov, and Fyodor Yarochkin
Regular cybercriminals appear to be taking a page from targeted attack actors’ playbooks — or rather, toolkits — to maximize their profits from illicit activities like cryptojacking.
One of the differences between regular cybercrime and targeted attacks is intent: The former will almost always have immediate financial gain as its main motivation while the latter will have other goals, for example, intellectual property theft. Furthermore, the mindsets of the threat actors can be very different. Regular cybercriminals will typically need to think of how they can compromise as many individual devices as possible (for example, to deliver ransomware, coin miners, or banking trojans) while targeted attack threat actors will need to plan how to infiltrate and gain full access to corporate networks and remain as discreet as possible.
In addition, targeted attack campaigns often involve extensive planning as well as the creation and use of highly specialized tools. On the other hand, normal threat actors might not have the ability or resources to plan sophisticated campaigns and their tools are more generic in nature and are often available in underground markets.
However, we recently came across evidence of a large-scale cybercrime activity that appears to combine targeted attack tools and regular cybercrime: The attackers distribute typical malware such as cryptocurrency miners and ransomware by making use of sophisticated tools that were previously mostly seen in targeted attacks. In the cases we identified, the threat actors were using a package of tools from the Equation group (which was publicly leaked by the Shadow Brokers) to compromise a large number of machines running outdated versions of Microsoft Windows OS. The technique of using advanced tools to spread more ubiquitous types of malware is a trend we have been observing lately. In fact, earlier this month we found and analyzed a malware family we called BlackSquid, which made use of well-known exploits and vulnerabilities to drop a cryptocurrency miner. The findings we discuss in this entry reinforce our suspicions that entry-level cybercriminals are gaining easy access to what we can consider “military-grade” tools — and are using them for seemingly ordinary cybercrime activity.
The activity we observed involves a cybercrime campaign that targets companies across the globe to spread a cryptocurrency miner for monetary purposes. The campaign features some interesting characteristics. For one, it only targets companies — we did not find any instances of individual users being targeted. And for another, all of the compromised machines were running outdated versions of Microsoft Windows OS, still vulnerable to already patched vulnerabilities. In addition, the campaign uses Equation group tools to deliver a cryptocurrency miner to organizations around the world.
Infection and proliferation
One of the first binaries we detected on the infected machines seems to be the possible culprit of the attack — a variant of Vools (Trojan.Win32.VOOLS.SMAL01), which is an EternalBlue-based backdoor that is used to deliver cryptocurrency miners and other malware. We also found a number of other tools in the infected systems, mainly the password dumping tool Mimikatz and Equation group tools. The final payload deployed on compromised systems is a cryptocurrency miner. Using data from the Trend Micro Smart Protection Network
Smart Protection Network security architecture, we can confirm that all of the compromised systems appear to be on internal segments of compromised networks.
security architecture, we can confirm that all of the compromised systems appear to be on internal segments of compromised networks.
While we could not confirm the origin of the infection, during our research we managed to find a sample that seems to be an installer which sends an HTTP request to the following server:
- log.boreye[.]com/ipc.html?mac={MAC address}&ip={IP address}&host={host}&tick=6min&c=error_33
However, we have been unable to retrieve any miners from the URL at the time of writing. Furthermore, the site is already inactive and have possibly been migrated to a different location by the threat actors behind the attack.
We identified a common file located in the main Windows folder of all the infected machines:
- C:WindowsNetworkDistributionDiagnostics.txt
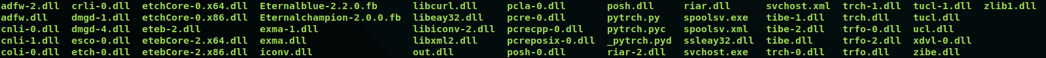
The .TXT file extension used is just a trick to avoid detection. The file is in fact a ZIP archive file that contains several files (the Equation toolkit components), as shown in the image below. (Notice the presence of many familiar names such as EternalBlue and EternalChampion.) On the other hand, the DLL files, which we observed were being dropped on the target machine, match the contents of a folder in the same GitHub repository as the leak’s.
Figure 1. The files located inside the zip archive
All these files are freely accessible for everyone on the internet to use. Although the vulnerabilities they exploit have already been patched, they can still be used successfully on systems that have not applied the update.
The cryptocurrency miner
Since we began tracking it in March 2019, we found more than 80 different files in the wild that are involved in the campaign based on their hashes. All these files are variants of the open-source XMRig (Monero) miner, which is used at scale by numerous cybercriminals worldwide. These variants are detected as either Coinminer.Win32.MALXMR.SMBM4 or Coinminer.Win64.TOOLXMR.SMA.
Configurations from the samples we found reveal a number of mining servers such as the following:
- coco[.]miniast[.]com:443
- iron[.]tenchier[.]com:443
- cake[.]pilutce[.]com:443
- pool[.]boreye[.]com:53
Another one, though we do not have a sample, is log.miniast[.]com.
Interestingly enough, the first three domains were registered on March 17, 2019, which is the date the campaign started based on our observations. These domains were registered anonymously while the older domain boreye[.]com was registered on October 17, 2018 using an email address that has only been used to register that single domain. User credentials are needed to connect to the mining server, but only the password is needed to retrieve new hashes.
Figure 2 shows the configurations we observed with the miner binaries used by the attacker.
Note: The passwords have been removed.
Figure 2. Screenshot of the configurations used by the cryptocurrency miner binaries
As can be seen in Figure 2, the usernames used are very similar. In addition, they all use the same password, which is a good indication that the same threat actor handles all the samples. The miner always uses the name dllhostex.exe. Furthermore, the binary is always located either in the “system32” or in the “SysWOW64” folder of the infected Windows machine, depending on the miner variant.
The targets of the campaign
The campaign seems to be widespread, with targets located in all regions of the world. Countries with large populations such as China and India also had the most number of organizations being targeted. This seems to indicate that the threat actors weren’t selective with their victims, opting for a “shotgun” method of attack, rampaging through the internal networks of compromised organizations rather than seeking out individual targets.
Figure 3. Distribution of targeted organizations according to country
The campaign also targeted businesses across a wide range of industries, including education, communication and media, banking, manufacturing, and technology. Again, rather than concentrate on specific industries, the attackers happen to choose targets that used obsolete or unpatched software. A large majority (roughly 83%, including all versions) of affected computers were running Windows Server 2003 SP2. This was followed by Windows 7 Ultimate Professional SP1 and Windows XP Professional.
Conclusion
While it takes some skill to deploy a large-scale campaign, it requires almost none to use tools such as the sophisticated ones leaked from the Equation group. The easy availability of these tools in the underground cybercrime markets, where ready-to-use mining servers are also being sold, allow even run-of-the-mill cybercriminals the ability to make use of them for seemingly “regular” cybercrime activity. As we discussed in our paper entitled “Security in the Era of Industry 4.0: Dealing With Threats to Smart Manufacturing Environments,” a number of industries depend on running significantly outdated systems, rendering them vulnerable to exploits despite the fact that the vulnerabilities already have patches.
The presence of automated attack platforms and the use of lateral movement techniques in compromised infrastructure for ubiquitous threats such as cryptocurrency miners and ransomware mean that even internal networks with vulnerable systems become easy targets for cybercriminals. The campaign we discussed in this post is only one of many we have observed in recent months. It shouldn’t come as a surprise to see more instances of non-professional threat actors using professional tools to make their attacks more effective. Given what we’ve observed, we cannot stress enough the need for organizations to update their systems as soon as possible to minimize risk and prevent these kinds of threats from affecting their systems.
Trend Micro Solutions
Trend Micro endpoint solutions such as the Trend Micro Smart Protection Suites and Worry-Free Business Security can protect users and businesses from threats such as cryptocurrency miners by detecting malicious files and blocking all related malicious URLs. Enterprises can also monitor all ports and network protocols for advanced threats with the Trend Micro Deep Discovery
Business Security can protect users and businesses from threats such as cryptocurrency miners by detecting malicious files and blocking all related malicious URLs. Enterprises can also monitor all ports and network protocols for advanced threats with the Trend Micro Deep Discovery Inspector network appliance.
Inspector network appliance.
Indicators of Compromise (IoCs)
Network IOCs
- miniast[.]com:443
- tenchier[.]com:443
- boreye[.]com:80
- boreye[.]com:53
- pilutce[.]com:443
Coin miner sample hashes
| SHA256 | Detection |
| dd21a9ce1d87e3a7f9f2a592ec9dd642ca19aee4a60502c8df21d9c25f9acf86 | Trojan.Win64.VOOLS.AF |
| 2af73c8603e1d51661b0fffc09be306797558204bcbd4f95dd2dfe8363901606 | Trojan.Win64.VOOLS.AB |
| ed2febf310ae90739002b9ddb07a29d0b2c8e92462ae4a0a6dcc19cc537ddef3 | Trojan.Win64.VOOLS.AB |
| 007f81debf1c984c5b4d5b84d6a8c06bcdf84d1a4cccdd9633e45de35015faf3 | PE_VIRUX.R-3 |
| 125f93883ccccb3c33964c8bcdd17b409b53fbc44de1e3b4afd7dfe79aa358cd | Coinminer.Win64.TOOLXMR.SMA |
| 1ac26e86540610d1293c421ed05c13cd6ed51759be153c45d194ff7552c88855 | Coinminer.Win64.TOOLXMR.SMA |
| 4c3575c7b6c530603e4cd76c7dcaed12fc5ebadbf4d4d6b46352eb08458683e8 | Coinminer.Win64.TOOLXMR.SMA |
| 4e46cec7f6e7fa13c10e808f0da104a8c810b7ef17c40d0e9a908453be87e7f4 | Coinminer.Win64.TOOLXMR.SMA |
| 5472f9ba3bc623450cc208669dacddb1b6a73ffe4dc705b85cf41637070fda28 | Coinminer.Win64.TOOLXMR.SMA |
| 572c3943f70a3e362d9bf195ce37cec68074235eb1abba9f0cdbb91f5231a572 | Coinminer.Win64.TOOLXMR.SMA |
| 5db45fa654910495592cf1ca00d7ef537708c38c4803d10d89eaa0ddba0e7d8c | Coinminer.Win64.TOOLXMR.SMA |
| 6ee5c5724ecc70f77aadcf00c77829e5313f44c61b2720113ada0c8263ac662c | Coinminer.Win64.TOOLXMR.SMA |
| 7ced0990ac94f36fab21821395f543f3a06be486c9f34cdc137874912573fb27 | Coinminer.Win64.TOOLXMR.SMA |
| 7f5bddeb0c9ecde4d64ddac8b046859fb1627811d96c29dfa2b88102740571ce | Coinminer.Win64.TOOLXMR.SMA |
| 94af094fc02cfe85a80f2f90d408f9598f9d77def36155e16a90e2bd8f8fdcce | Coinminer.Win64.TOOLXMR.SMA |
| 975dc8ecda9a9c15d19c4d9d67f961366d2f0ac1074b5eb5d3b36e653092a6a3 | Coinminer.Win64.TOOLXMR.SMA |
| bafe63e8fd76f1c9010137e6cd5137655ea12ab5c25d0b86700627b2ebad2be0 | Coinminer.Win64.TOOLXMR.SMA |
| ce5025a484b3e2481e248dee404e6d321b6d7f58bae77b284ec9e602672e6a10 | Coinminer.Win64.TOOLXMR.SMA |
| ce8cb7c8dc29b9e4feab463fdf53b569b69e6a5c4ab0e50513b264563d74a6ac | Coinminer.Win64.TOOLXMR.SMA |
| 9af55d177e7d7628dc63f7753de4780031073098e1c674e619826cb97c190744 | Coinminer.Win64.TOOLXMR.AR |
| f81dd3e5b0507d78815f5909ab442545cb3f5262397abd89b5947e1e7b3fef12 | Coinminer.Win64.TOOLXMR.AQ |
| 35d10df58e340b6a7d69e590852b84a6a02f774306c3eb29e60e6b24740456eb | Coinminer.Win32.MALXMR.SMBM4 |
| 13800d1075e56f9bd0d87b2e85555040233e8b2ec679770101d046ffa4e39582 | Coinminer.Win32.MALXMR.SMBM4 |
| 199e0419622e108ffdd7c9de571931d9aedc4f980a602766c0fdcb17bdddfc2a | Coinminer.Win32.MALXMR.SMBM4 |
| 1bc9762470423393521d9aa64d505501d201d3cb50c8e6576d4381590b090d75 | Coinminer.Win32.MALXMR.SMBM4 |
| 2d6a5eb8a78cddee8ce90321aab80f85784b11a87b00fde75c4c457998a5aebd | Coinminer.Win32.MALXMR.SMBM4 |
| 3638ee8c0153b2763eb36246d9ffe4f7ec6d1f7e76876fb6f579c45e6e55e260 | Coinminer.Win32.MALXMR.SMBM4 |
| 469e7ac4b5bad89e305e1e7ec65773844f3d639e84476da4b1fdf442a7c28504 | Coinminer.Win32.MALXMR.SMBM4 |
| 59e3cf8f342a2bb5ce22bb03f8671568f68751f807002f9b329ed58e12a8831c | Coinminer.Win32.MALXMR.SMBM4 |
| 5cd9ff29454e84923d4178484ecfb3bc48561d4401fa94b98f9d2693d47a740a | Coinminer.Win32.MALXMR.SMBM4 |
| 6173542183c304ac2efc0348df799c1e3dea508cceaaac461bd509dc436d4edf | Coinminer.Win32.MALXMR.SMBM4 |
| 82c0b0fbb0f44ad2bc46c8b105f167f0feadf936ff811f97aab3a9a6cccc2fb2 | Coinminer.Win32.MALXMR.SMBM4 |
| 87488d9ad54b88e5488c18d8de6a338eaf4fe7bdeec2df7eeaf90380de1533b6 | Coinminer.Win32.MALXMR.SMBM4 |
| 8d402a3871bada94d84dd8a7c29361f27b75ac37394f6de059b06afb340fe3d6 | Coinminer.Win32.MALXMR.SMBM4 |
| 9853e7bd0906cf92d2767fa55ee0a645f23099b37d59654d3c388d897a19fb1e | Coinminer.Win32.MALXMR.SMBM4 |
| af21fb86d48b60ee58084570fba12cf3dbc3992c713421a265cd451c169967d2 | Coinminer.Win32.MALXMR.SMBM4 |
| cf60518d2a22631d0539964ff97bc396b44ef5f6979f7a9e59e03c89598db0bf | Coinminer.Win32.MALXMR.SMBM4 |
| ec85ec44771401d4a71cb7f8bc3597d55ec02b84178464ab33161c77c4f51f0b | Coinminer.Win32.MALXMR.SMBM4 |
| ecfcd390712f6ac57b822ef519063f8e9151e90549e245e4e2a70d02ff584634 | Coinminer.Win32.MALXMR.SMBM4 |
The post Advanced Targeted Attack Tools Found Being Used to Distribute Cryptocurrency Miners appeared first on .