Apple and Microsoft recently released software updates to fix dozens of security holes in their operating systems. Microsoft today patched at least 60 vulnerabilities in its Windows OS. Meanwhile, Apple’s new macOS Sonoma addresses at least 68 security weaknesses, and its latest update for iOS fixes two zero-day flaws. Last week, Apple pushed out an… Continue reading Patch Tuesday, March 2024 Edition
Category: Anti-malware
Auto Added by WPeMatico
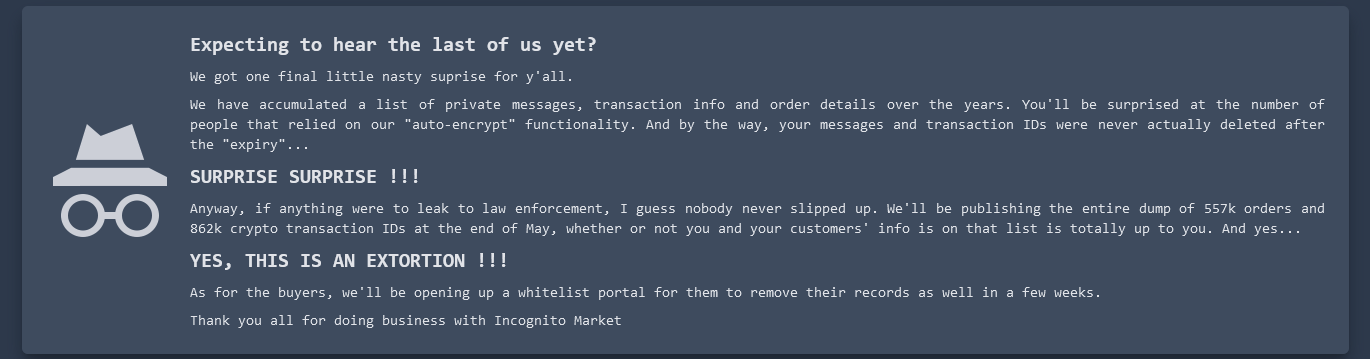
Incognito Darknet Market Mass-Extorts Buyers, Sellers
Borrowing from the playbook of ransomware purveyors, the darknet narcotics bazaar Incognito Market has begun extorting all of its vendors and buyers, threatening to publish cryptocurrency transaction and chat records of users who refuse to pay a fee ranging from $100 to $20,000. The bold mass extortion attempt comes just days after Incognito Market administrators… Continue reading Incognito Darknet Market Mass-Extorts Buyers, Sellers
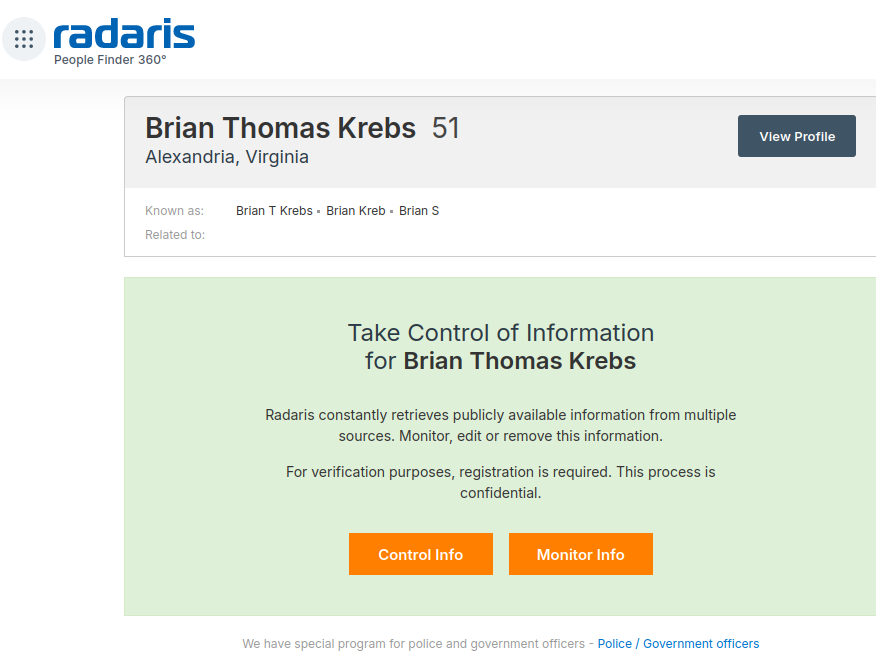
A Close Up Look at the Consumer Data Broker Radaris
If you live in the United States, the data broker Radaris likely knows a great deal about you, and they are happy to sell what they know to anyone. But how much do we know about Radaris? Publicly available data indicates that in addition to running a dizzying array of people-search websites, the co-founders of… Continue reading A Close Up Look at the Consumer Data Broker Radaris
BlackCat Ransomware Group Implodes After Apparent $22M Payment by Change Healthcare
There are indications that U.S. healthcare giant Change Healthcare has made a $22 million extortion payment to the infamous BlackCat ransomware group (a.k.a. “ALPHV“) as the company struggles to bring services back online amid a cyberattack that has disrupted prescription drug services nationwide for weeks. However, the cybercriminal who claims to have given BlackCat access… Continue reading BlackCat Ransomware Group Implodes After Apparent $22M Payment by Change Healthcare
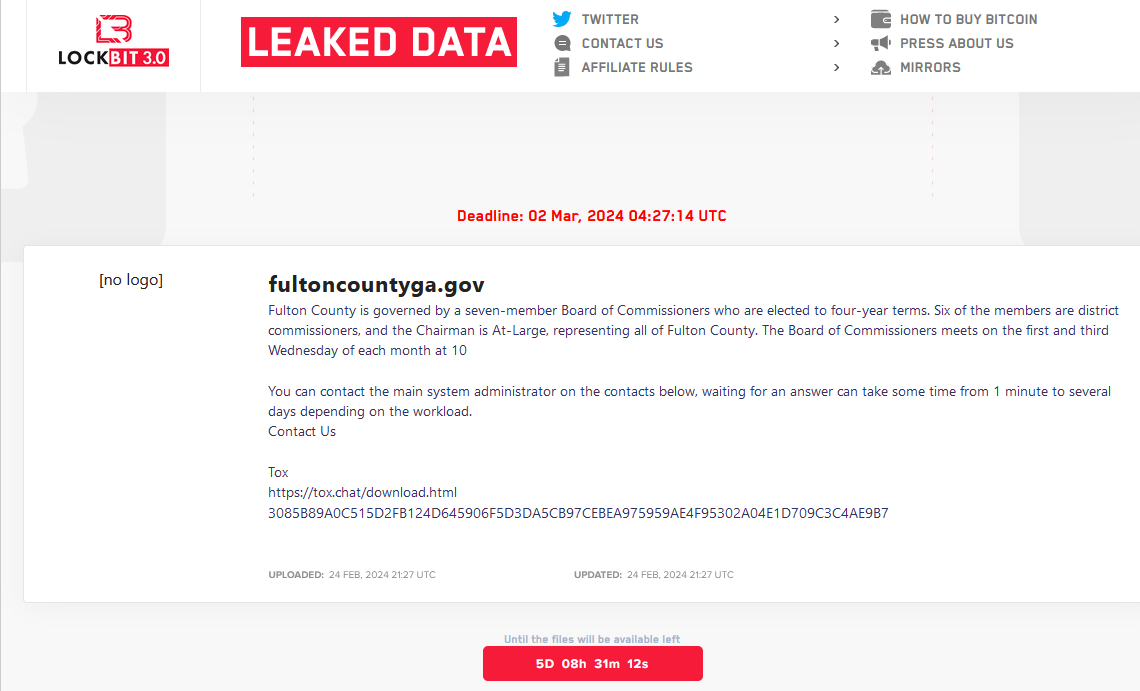
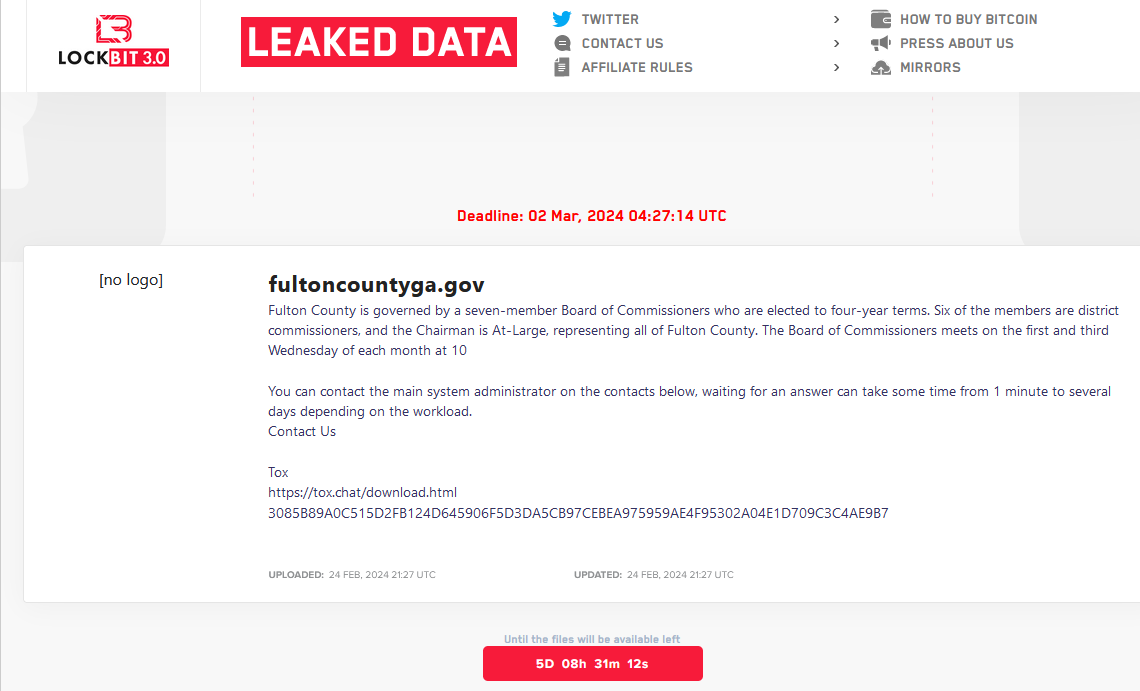
Fulton County, Security Experts Call LockBit’s Bluff
The ransomware group LockBit told officials with Fulton County, Ga. they could expect to see their internal documents published online this morning unless the county paid a ransom demand. LockBit removed Fulton County’s listing from its victim shaming website this morning, claiming the county had paid. But county officials said they did not pay, nor… Continue reading Fulton County, Security Experts Call LockBit’s Bluff
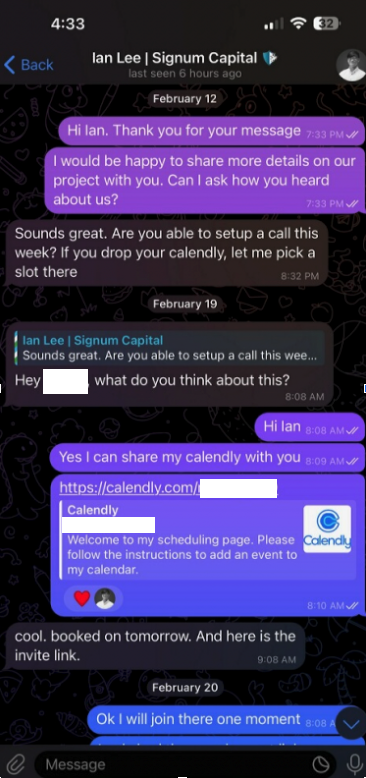
Calendar Meeting Links Used to Spread Mac Malware
Malicious hackers are targeting people in the cryptocurrency space in attacks that start with a link added to the target’s calendar at Calendly, a popular application for scheduling appointments and meetings. The attackers impersonate established cryptocurrency investors and ask to schedule a video conference call. But clicking the meeting link provided by the scammers prompts… Continue reading Calendar Meeting Links Used to Spread Mac Malware
FBI’s LockBit Takedown Postponed a Ticking Time Bomb in Fulton County, Ga.
The FBI’s takedown of the LockBit ransomware group last week came as LockBit was preparing to release sensitive data stolen from government computer systems in Fulton County, Ga. But LockBit is now regrouping, and the gang says it will publish the stolen Fulton County data on March 2 unless paid a ransom. LockBit claims the… Continue reading FBI’s LockBit Takedown Postponed a Ticking Time Bomb in Fulton County, Ga.
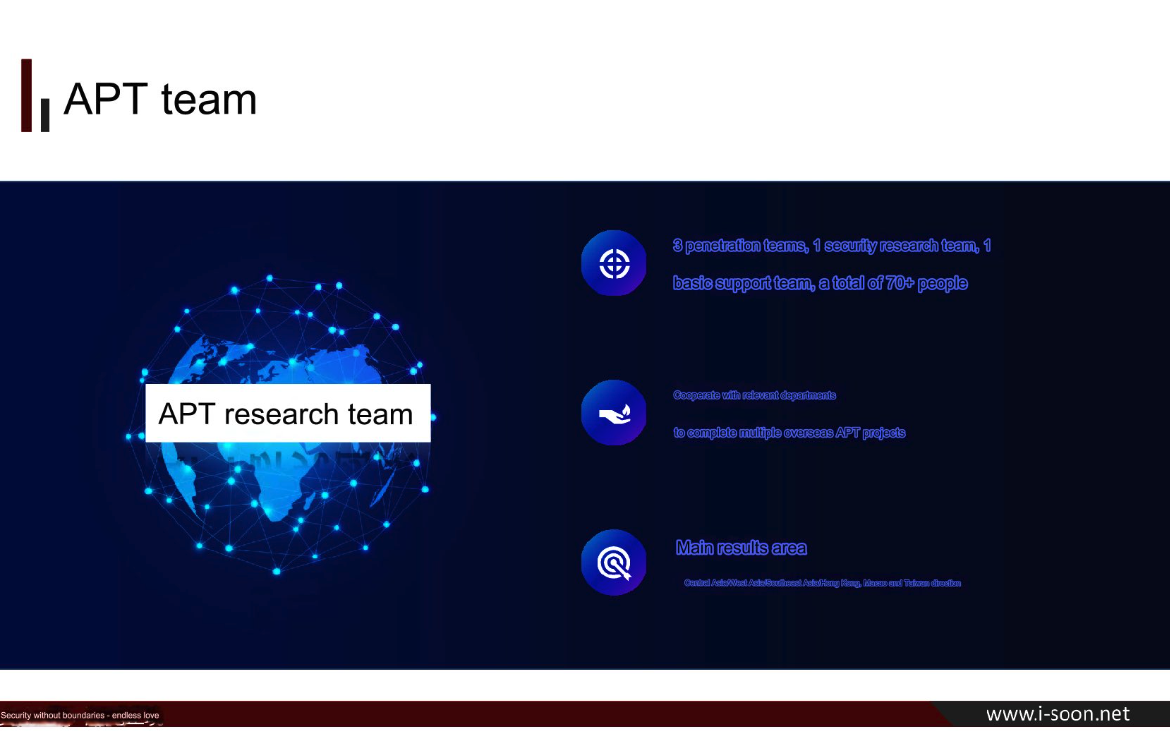
New Leak Shows Business Side of China’s APT Menace
A new data leak that appears to have come from one of China’s top private cybersecurity firms provides a rare glimpse into the commercial side of China’s many state-sponsored hacking groups. Experts say the leak illustrates how Chinese government agencies increasingly are contracting out foreign espionage campaigns to the nation’s burgeoning and highly competitive cybersecurity… Continue reading New Leak Shows Business Side of China’s APT Menace
Feds Seize LockBit Ransomware Websites, Offer Decryption Tools, Troll Affiliates
U.S. and U.K. authorities have seized the darknet websites run by LockBit, a prolific and destructive ransomware group that has claimed more than 2,000 victims worldwide and extorted over $120 million in payments. Instead of listing data stolen from ransomware victims who didn’t pay, LockBit’s victim shaming website now offers free recovery tools, as well… Continue reading Feds Seize LockBit Ransomware Websites, Offer Decryption Tools, Troll Affiliates
U.S. Internet Leaked Years of Internal, Customer Emails
The Minnesota-based Internet provider U.S. Internet Corp. has a business unit called Securence, which specializes in providing filtered, secure email services to businesses, educational institutions and government agencies worldwide. But until it was notified last week, U.S. Internet was publishing more than a decade’s worth of its internal email — and that of thousands of… Continue reading U.S. Internet Leaked Years of Internal, Customer Emails