The Minnesota-based Internet provider U.S. Internet Corp. has a business unit called Securence, which specializes in providing filtered, secure email services to businesses, educational institutions and government agencies worldwide. But until it was notified last week, U.S. Internet was publishing more than a decade’s worth of its internal email — and that of thousands of… Continue reading U.S. Internet Leaked Years of Internal, Customer Emails
Fat Patch Tuesday, February 2024 Edition
Microsoft Corp. today pushed software updates to plug more than 70 security holes in its Windows operating systems and related products, including two zero-day vulnerabilities that are already being exploited in active attacks. Top of the heap on this Fat Patch Tuesday is CVE-2024-21412, a “security feature bypass” in the way Windows handles Internet Shortcut… Continue reading Fat Patch Tuesday, February 2024 Edition
Juniper Support Portal Exposed Customer Device Info
Until earlier this week, the support website for networking equipment vendor Juniper Networks was exposing potentially sensitive information tied to customer products, including which devices customers bought, as well as each product’s warranty status, service contracts and serial numbers. Juniper said it has since fixed the problem, and that the inadvertent data exposure stemmed from… Continue reading Juniper Support Portal Exposed Customer Device Info
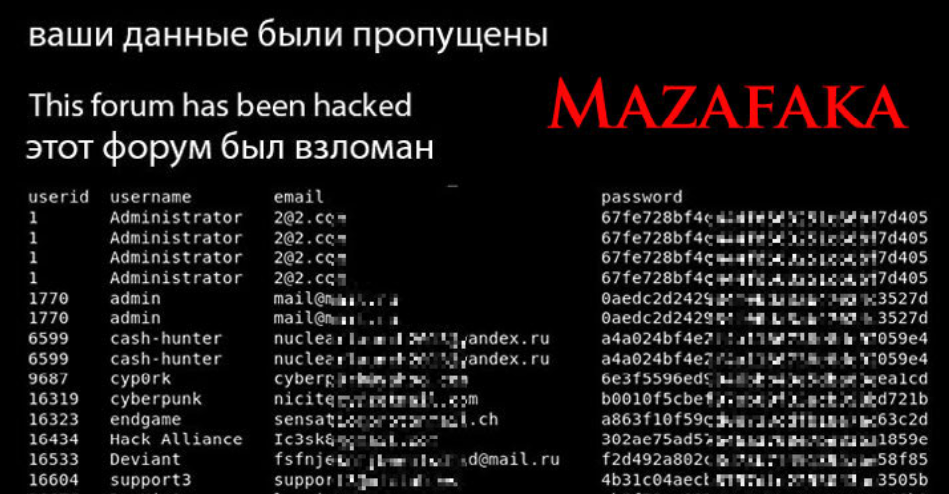
From Cybercrime Saul Goodman to the Russian GRU
In 2021, the exclusive Russian cybercrime forum Mazafaka was hacked. The leaked user database shows one of the forum’s founders was an attorney who advised Russia’s top hackers on the legal risks of their work, and what to do if they got caught. A review of this user’s hacker identities shows that during his time… Continue reading From Cybercrime Saul Goodman to the Russian GRU
Arrests in $400M SIM-Swap Tied to Heist at FTX?
Three Americans were charged this week with stealing more than $400 million in a November 2022 SIM-swapping attack. The U.S. government did not name the victim organization, but there is every indication that the money was stolen from the now-defunct cryptocurrency exchange FTX, which had just filed for bankruptcy on that same day. A graphic… Continue reading Arrests in $400M SIM-Swap Tied to Heist at FTX?
Fla. Man Charged in SIM-Swapping Spree is Key Suspect in Hacker Groups Oktapus, Scattered Spider
On Jan. 9, 2024, U.S. authorities arrested a 19-year-old Florida man charged with wire fraud, aggravated identity theft, and conspiring with others to use SIM-swapping to steal cryptocurrency. Sources close to the investigation tell KrebsOnSecurity the accused was a key member of a criminal hacking group blamed for a string of cyber intrusions at major… Continue reading Fla. Man Charged in SIM-Swapping Spree is Key Suspect in Hacker Groups Oktapus, Scattered Spider
Who is Alleged Medibank Hacker Aleksandr Ermakov?
Authorities in Australia, the United Kingdom and the United States this week levied financial sanctions against a Russian man accused of stealing data on nearly 10 million customers of the Australian health insurance giant Medibank. 33-year-old Aleksandr Ermakov allegedly stole and leaked the Medibank data while working with one of Russia’s most destructive ransomware groups,… Continue reading Who is Alleged Medibank Hacker Aleksandr Ermakov?
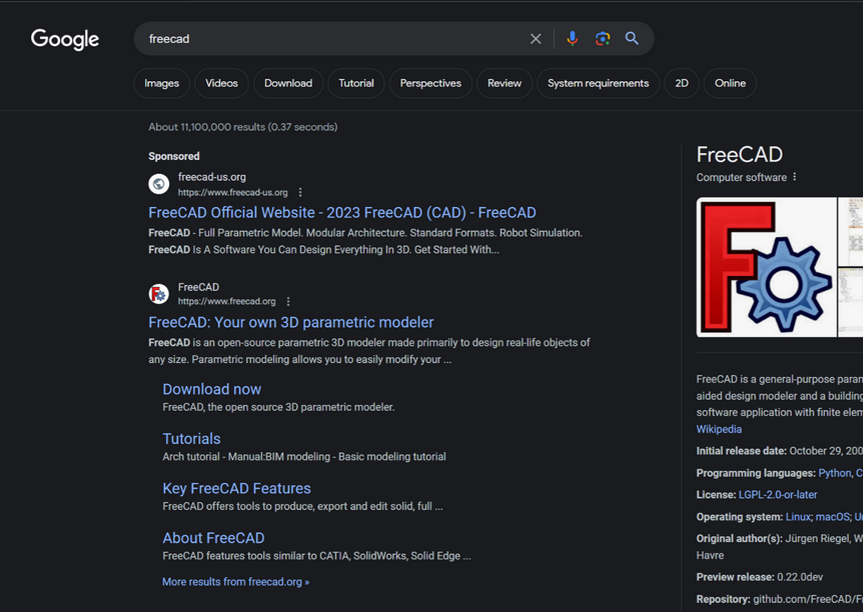
Using Google Search to Find Software Can Be Risky
Google continues to struggle with cybercriminals running malicious ads on its search platform to trick people into downloading booby-trapped copies of popular free software applications. The malicious ads, which appear above organic search results and often precede links to legitimate sources of the same software, can make searching for software on Google a dicey affair.… Continue reading Using Google Search to Find Software Can Be Risky
Canadian Man Stuck in Triangle of E-Commerce Fraud
A Canadian man who says he’s been falsely charged with orchestrating a complex e-commerce scam is seeking to clear his name. His case appears to involve “triangulation fraud,” which occurs when a consumer purchases something online — from a seller on Amazon or eBay, for example — but the seller doesn’t actually own the item… Continue reading Canadian Man Stuck in Triangle of E-Commerce Fraud
E-Crime Rapper ‘Punchmade Dev’ Debuts Card Shop
The rapper and social media personality Punchmade Dev is perhaps best known for his flashy videos singing the praises of a cybercrime lifestyle. With memorable hits such as “Internet Swiping” and “Million Dollar Criminal” earning millions of views, Punchmade has leveraged his considerable following to peddle tutorials on how to commit financial crimes online. But… Continue reading E-Crime Rapper ‘Punchmade Dev’ Debuts Card Shop